
During the COVID-19 lockdowns, everyone (especially gamers) looked for alternative ways to socialize since PC cafes, gaming houses, bars/pubs, and other social gathering points were all closed since the early months of 2020. The availability of cross-platform gameplay, as well as gaming-friendly social platforms (e.g., Discord), enabled a common element of interaction.
In April, Steam reported a record-setting day, shortly after the previous record was set in March. On 4 April, 24 million players were online, with 8 million of them in-game at the time the record was set. In fact, if you look at the Steam metrics in Figure 1, you can see that Q1 2020 — when most of the pandemic-based lockdowns took place — included steady increases in gamer interaction and consistent play times. This was the reason which has spiked the rate of accounts being compromised .
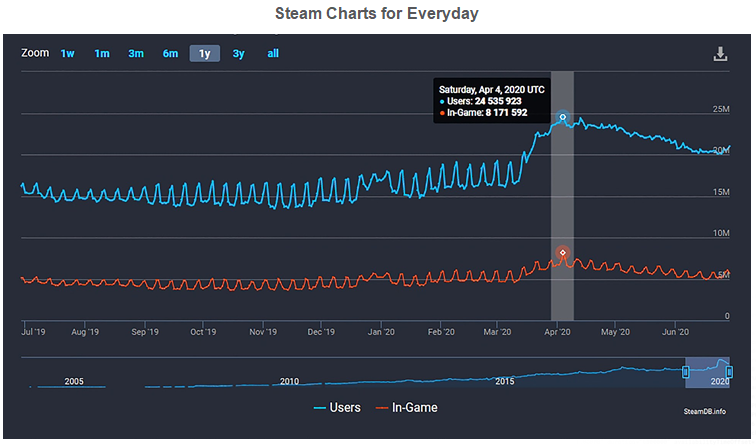 Steam Fig.1
Steam Fig.1
In the spring of 2020, working with esports company DreamHack, Akamai sent a survey to gamers to gather their insights on security as it relates to their gaming experience. The initial survey results include 1,253 responses from European gamers, followed by a second set of questions and answers from 369 of the original respondents.
Akamai published the State of the Internet / Security report, Gaming: You Can’t Solo Security. The report reveals that high volumes of attacks were used to target video game companies and players between 2018 and 2020. It also notes an uptick in attack traffic that correlates with COVID-19-related lockdowns.

“The fine line between virtual fighting and real world attacks is gone. Criminals are launching relentless waves of attacks against games and players alike in order to compromise accounts, steal and profit from personal information and in-game assets, and gain competitive advantages. It’s vital that gamers, game publishers, and game services work in concert to combat these malicious activities through a combination of technology, vigilance, and good security hygiene,” said Akamai security researcher and author of the State of the Internet / Security report Steve Ragan.
Key findings of the report:
- Akamai observed more than 100 billion credential stuffing attacks from July 2018 to June 2020.
- Nearly 10 billion of those attacks targeted the gaming sector.
- 10.6 billion web application attacks across its customers between July 2018 and June 2020, more than 152 million of which were directed toward the gaming industry.
- 55 per cent of the respondents who identify as “frequent players” admitted to having had an account compromised at some point; of those, only 20 per cent expressed being “worried” or “very worried” about it.
- 54 per cent of the survey participants who have been hacked say that security is the shared responsibility of the gamer and the game developer/company.
- The gaming-related DDoS attacks spiked during holiday periods, as well as typical school vacation seasons.
- To execute this type of attack, criminals attempt to access games and gaming services using lists of username and password combinations that are typically available for purchase via nefarious websites and services.

- Game players themselves are subjected to a steady barrage of criminal activity, largely through credential stuffing and phishing attacks.
- In phishing method, bad actors create legitimate-looking websites related to a game or gaming platform with the goal of tricking players into revealing their login credentials.
- A notable spike in credential stuffing activity occurred as isolation protocols were instituted around the world. Much of the traffic was the result of criminals testing credentials from old data breaches in attempts to compromise new accounts created using an existing username and password combinations.
- Once hacked 49.1 per cent survey participants believe they will lose credit card information, 47.7 per cent believe that they will lose account information, 42.1 per cent believe they will lose game items and 1.7 per cent have other miscellaneous reasons.
- Behind the cyber security in gaming, 67.4 per cent find themselves as responsible, 76.2 per cent find gaming companies are responsible, 50 per cent find themselves and the company responsible, and so on.
Web attacks are constant. Credential stuffing attacks can turn data breaches from the days of old (meaning last week) into new incidents that impact thousands (sometimes millions) of people and organisations of all sizes. DDoS attacks disrupt the world of instant communication and connection.
These are problems that gamers, consumers, and business leaders face on a daily basis. This year, these issues have only gotten worse, and the stress
caused by them was compounded by an invisible deadly threat known as COVID-19.
